Reversible Encryption
Reversible Encryption - Instantly, remotely, and REVERSIBLY encode files until returned to your control.
Administrators can proactively act to defend critical information on a missing device without delay or concern of causing data loss.
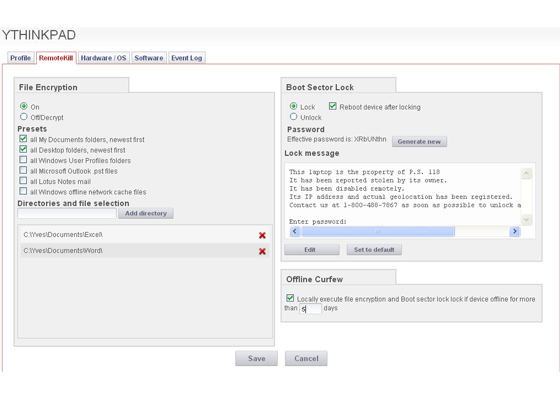
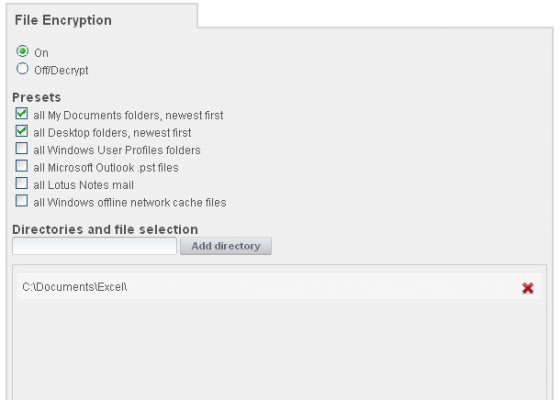
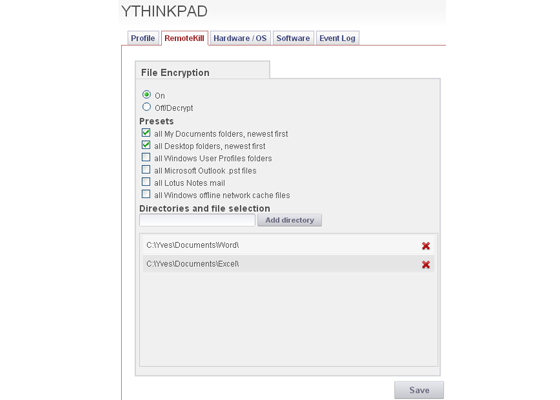
 STOPMonitor Pro does not defend data with an “all or nothing” or “just erase it” approach. From the Enterprise Console, administrators can set machines to encrypt their data at the directory or file level. Using military grade file encryption following the Advanced Encryption Standard (AES 128),
mobile device data is protected from access by unauthorized users or thieves, but the encryption remains fully reversible should a missing device be recovered. Once a computer is confirmed as in legitimate hands, administrators can remotely reverse the file encryption and reunite users with their data.
STOPMonitor Pro does not defend data with an “all or nothing” or “just erase it” approach. From the Enterprise Console, administrators can set machines to encrypt their data at the directory or file level. Using military grade file encryption following the Advanced Encryption Standard (AES 128),
mobile device data is protected from access by unauthorized users or thieves, but the encryption remains fully reversible should a missing device be recovered. Once a computer is confirmed as in legitimate hands, administrators can remotely reverse the file encryption and reunite users with their data.
 Because STOPMonitor protects data through non-destructive reversible encryption, administrators are free to take strong action the moment a threat is perceived without concern that a “bad call” might result in lost data. The administrator receives immediate confirmation from the device when the selected files or folders have been successfully encrypted.
Because STOPMonitor protects data through non-destructive reversible encryption, administrators are free to take strong action the moment a threat is perceived without concern that a “bad call” might result in lost data. The administrator receives immediate confirmation from the device when the selected files or folders have been successfully encrypted.
STOPMonitor’s encryption secures data directly without reliance on the operating system. This approach means that even if the drive is removed from a machine and placed in a different device, its data remains encrypted and safe.