Bootlock
Bootlock - Equip machines with data protection tools needed to defend themselves.
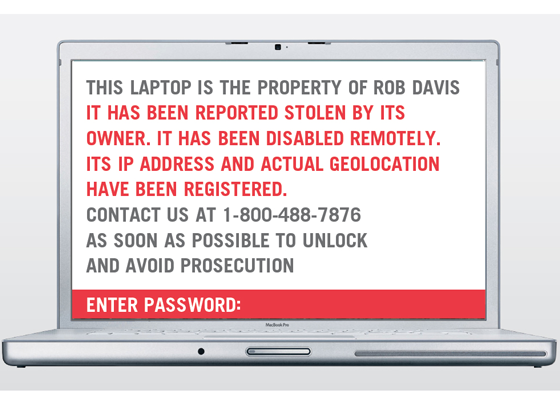
Total data security brings peace of mind. With Bootlock, mobile devices can be fully disabled so unauthorized persons can’t start or use them.
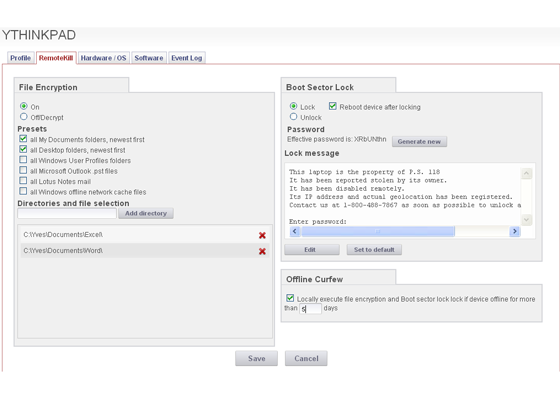
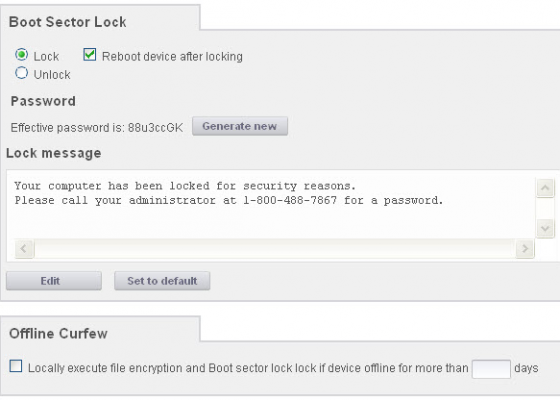
 STOPMonitor Bootlock is designed to provide the ultimate security. From the Enterprise Console, administrators can remotely, instantly reboot and lock out connected devices, effectively rendering them unstartable. Loading before the operating system, Bootlock makes it virtually impossible to circumvent protection. To pass the block, a password that is generated from the Enterprise Console must be entered on the target machine and verified by STOPMonitor. As a further level of security, the password is generated at the point of reactivation by the administrator, eliminating the possibility that a preexisting password has been compromised.
STOPMonitor Bootlock is designed to provide the ultimate security. From the Enterprise Console, administrators can remotely, instantly reboot and lock out connected devices, effectively rendering them unstartable. Loading before the operating system, Bootlock makes it virtually impossible to circumvent protection. To pass the block, a password that is generated from the Enterprise Console must be entered on the target machine and verified by STOPMonitor. As a further level of security, the password is generated at the point of reactivation by the administrator, eliminating the possibility that a preexisting password has been compromised.
 The Bootlock can be preset to take effect automatically if a device has not connected and checked in before a predetermined “offline curfew” number of days. With no need for a missing machine to establish a live connection, the lockdown procedure can be set to activate at the next reboot and then lock out the device eliminating any continued unauthorized use of the device. A customized, “Bootlock” message informs thieves (or no longer authorized users) that the machine has been locked until an administrator authorizes access by providing a new access password generated from the administration console.
The Bootlock can be preset to take effect automatically if a device has not connected and checked in before a predetermined “offline curfew” number of days. With no need for a missing machine to establish a live connection, the lockdown procedure can be set to activate at the next reboot and then lock out the device eliminating any continued unauthorized use of the device. A customized, “Bootlock” message informs thieves (or no longer authorized users) that the machine has been locked until an administrator authorizes access by providing a new access password generated from the administration console.
For the administrator, removal of an active Bootlock is as simple as targeting the recovered machine and clicking the “unlock” button. Simple for the administrator, impossible for unauthorized users.