Enterprise Console
Enterprise Console - Web-based administrative control and understanding of all technology assets
The central station for overseeing organizational assets, the Enterprise Console, provides administrators direct control over every protected device.
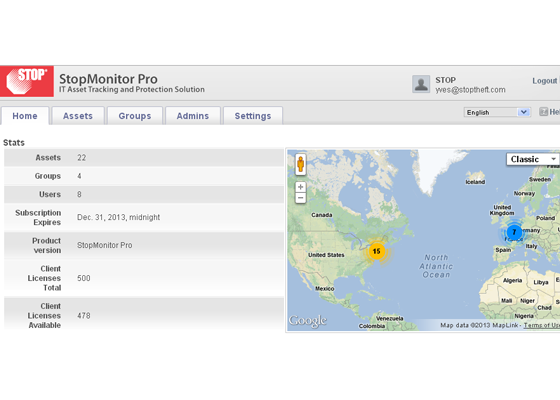
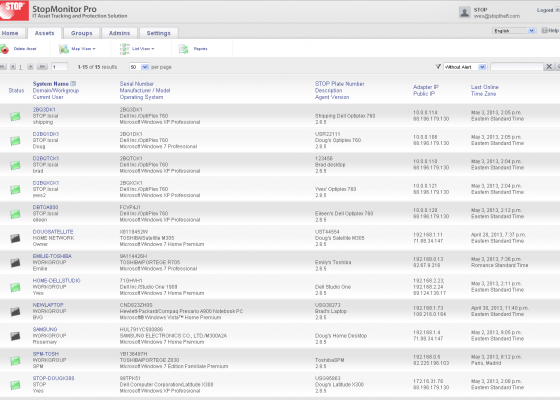
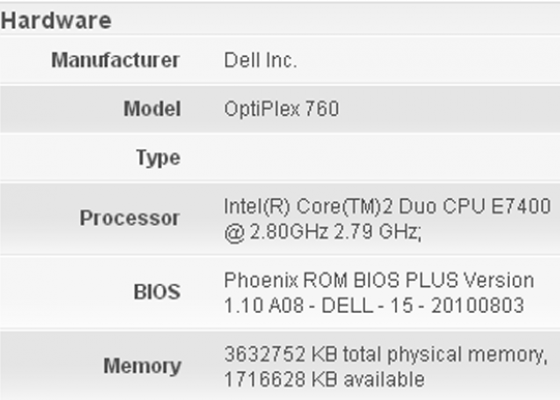
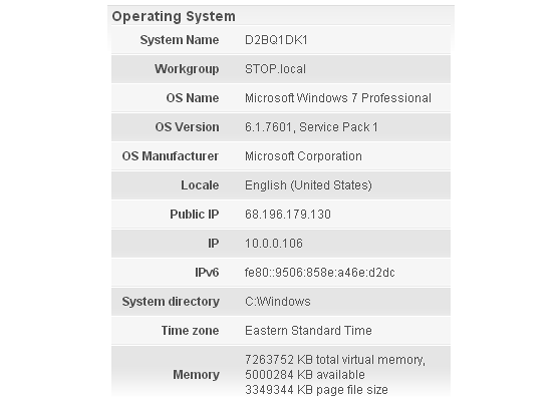
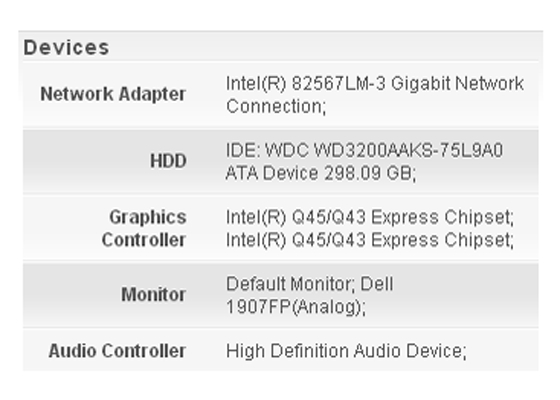
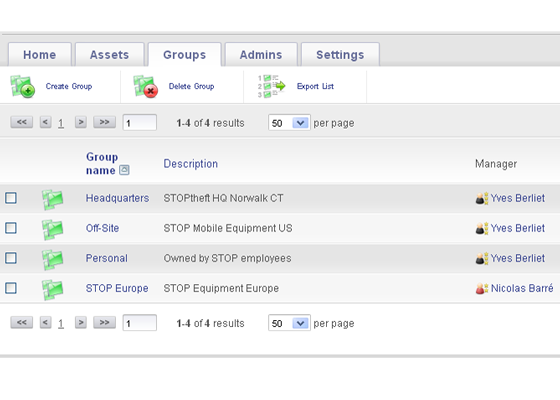
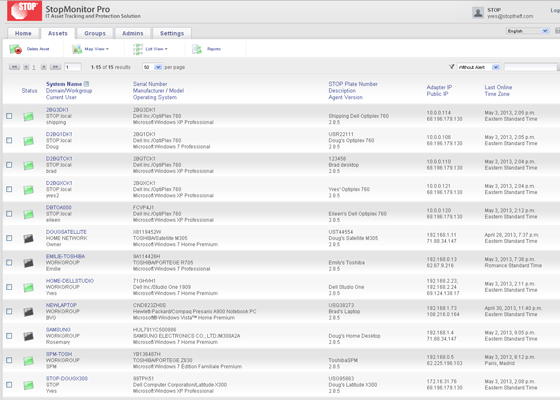
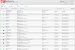
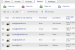
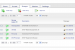
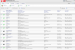
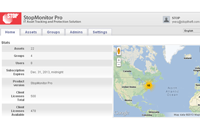 The central information view and functionality provided by the Enterprise Console is an unparalleled aid to administrators. Accessible from any web-connected location, it displays every important information element for managed computers collectively and individually. Asset management data such as user name, device name, hardware configuration, serial number, description, IP address, software, operating system version, current network connection status, and most recent connect time are all collected and granularly reported. Clear, and easy to use, STOPMonitor Pro allows administrators to see at-a-glance the full complement of computers under their supervision and to quickly filter the results to identify and target any group or single device.
The central information view and functionality provided by the Enterprise Console is an unparalleled aid to administrators. Accessible from any web-connected location, it displays every important information element for managed computers collectively and individually. Asset management data such as user name, device name, hardware configuration, serial number, description, IP address, software, operating system version, current network connection status, and most recent connect time are all collected and granularly reported. Clear, and easy to use, STOPMonitor Pro allows administrators to see at-a-glance the full complement of computers under their supervision and to quickly filter the results to identify and target any group or single device.
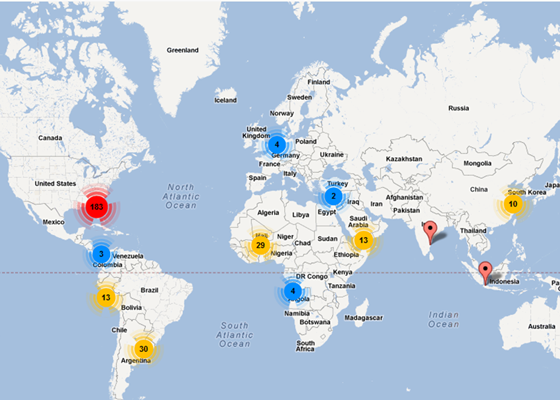
With the ability to manage up to 2.5 million devices, STOPMonitor Pro is capable of serving as the central asset control center for any sized organization.
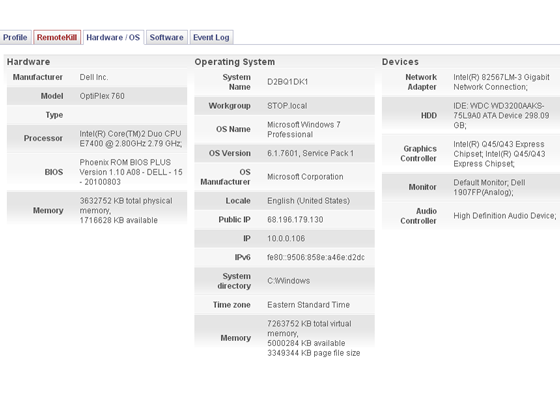
 Administrators can tailor their computer security using multiple approaches to provide enterprise level protection for both hardware and data. By accessing the web-based console from any desk, administrators can geolocate missing machines, target them and with a simple toggle, reversibly encrypt data the moment a threat is identified or even suspected. For constant, active defense, devices can be pre-set to lock down (via the Bootlock function), with files becoming reversibly encrypted if the device does not connect within a pre-determined number of days.
Administrators can tailor their computer security using multiple approaches to provide enterprise level protection for both hardware and data. By accessing the web-based console from any desk, administrators can geolocate missing machines, target them and with a simple toggle, reversibly encrypt data the moment a threat is identified or even suspected. For constant, active defense, devices can be pre-set to lock down (via the Bootlock function), with files becoming reversibly encrypted if the device does not connect within a pre-determined number of days.
When administrators are satisfied that the asset is safely returned or in authorized hands, they can simply return to the Enterprise Console and via password disable bootlocks or decrypt protected files.